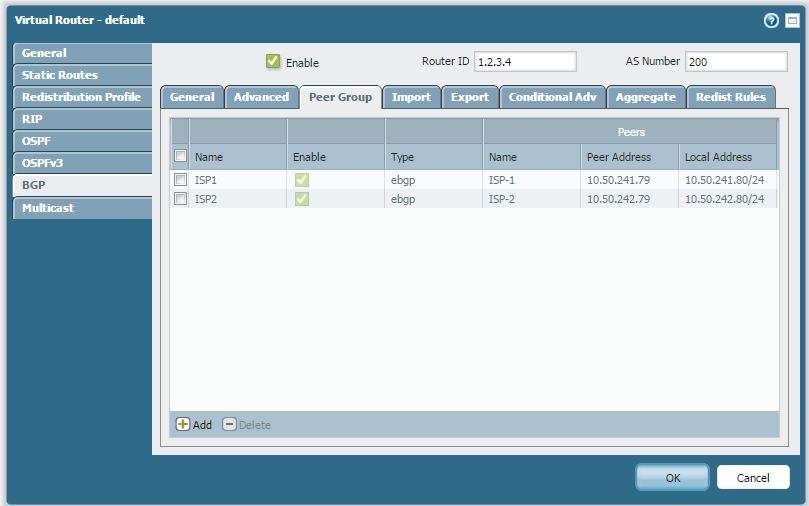
1. An easy way to check SSL negotiation details between a client and a server is to use openssl.
2. In a Linux system (ex: Kali Linux), use openssl s_client to verify the negotiation details.
3. Open a shell in linux
4. Commands used
a. #openssl
b. #s_client -connect www.systemstudio.com:443 –> NOTE : <domain name>:<443>
5. Sample output :
OpenSSL> s_client -connect www.systemstudio.com:443
CONNECTED(00000003)
depth=2 C = BE, O = GlobalSign nv-sa, OU = Root CA, CN = GlobalSign Root CA
verify return:1
depth=1 C = BE, O = GlobalSign nv-sa, CN = GlobalSign Domain Validation CA – SHA256 – G2
verify return:1
depth=0 OU = Domain Control Validated, CN = cc.sedoparking.com
verify return:1
—
Certificate chain
0 s:/OU=Domain Control Validated/CN=cc.sedoparking.com
i:/C=BE/O=GlobalSign nv-sa/CN=GlobalSign Domain Validation CA – SHA256 – G2
1 s:/C=BE/O=GlobalSign nv-sa/CN=GlobalSign Domain Validation CA – SHA256 – G2
i:/C=BE/O=GlobalSign nv-sa/OU=Root CA/CN=GlobalSign Root CA
—
Server certificate
—–BEGIN CERTIFICATE—–
MIIE8jCCA9qgAwIBAgISESGTb+pqujeMpyMkW48SWnhQMA0GCSqGSIb3DQEBCwUA
MGAxCzAJBgNVBAYTAkJFMRkwFwYDVQQKExBHbG9iYWxTaWduIG52LXNhMTYwNAYD
VQQDEy1HbG9iYWxTaWduIERvbWFpbiBWYWxpZGF0aW9uIENBIC0gU0hBMjU2IC0g
RzIwHhcNMTUxMTExMDg0NTQwWhcNMTcxMTExMDg0NTQwWjBAMSEwHwYDVQQLExhE
b21haW4gQ29udHJvbCBWYWxpZGF0ZWQxGzAZBgNVBAMTEmNjLnNlZG9wYXJraW5n
LmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBALSX9ixYi6cB09+r
yhtRS1lh0wd11WhccAWnPq0kXp7+PnkUkv+wjRFZ/bjk/l+LPO8HwPWLYhKlembV
54Fn+UJyvEpvBuEF7iX7+PW89Aymmx4/2Fggln4ozO3qFHpNBo/IJVet5YTMIqm7
PGNzR6V7NT8e8wGDqeFHKoEdxxIFNpXPNxCOPF2ZbFffATeIBqY+0QGB+NWM/emu
BYGkzkmoZRnHFH7+9INwCvPIo78xTInZQQMX1OvxX1AhEzw2U0JH9nVHLguQKuwr
u1uUMMQScx4o/0g2flmpMMa7Eep4Z+HJnuGE4NnBBzcg4M06kxByFWD1xULkYysO
b5907YMCAwEAAaOCAcQwggHAMA4GA1UdDwEB/wQEAwIFoDBJBgNVHSAEQjBAMD4G
BmeBDAECATA0MDIGCCsGAQUFBwIBFiZodHRwczovL3d3dy5nbG9iYWxzaWduLmNv
bS9yZXBvc2l0b3J5LzAdBgNVHREEFjAUghJjYy5zZWRvcGFya2luZy5jb20wCQYD
VR0TBAIwADAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwQwYDVR0fBDww
OjA4oDagNIYyaHR0cDovL2NybC5nbG9iYWxzaWduLmNvbS9ncy9nc2RvbWFpbnZh
bHNoYTJnMi5jcmwwgZQGCCsGAQUFBwEBBIGHMIGEMEcGCCsGAQUFBzAChjtodHRw
Oi8vc2VjdXJlLmdsb2JhbHNpZ24uY29tL2NhY2VydC9nc2RvbWFpbnZhbHNoYTJn
MnIxLmNydDA5BggrBgEFBQcwAYYtaHR0cDovL29jc3AyLmdsb2JhbHNpZ24uY29t
L2dzZG9tYWludmFsc2hhMmcyMB0GA1UdDgQWBBQOb+sP/EvKLwTF/twbuKVfMeHD
ajAfBgNVHSMEGDAWgBTqTnzUgC3lFYGGJoyCbcCYpM+XDzANBgkqhkiG9w0BAQsF
AAOCAQEAUctF7dn2Zc9Lgv2k/AIwLgDYdHLFJD0yOhHFKuuR4vYmGS3mQ0y42FDT
SP7wiZRqEb+UUt/BaXYwo/rcRZUEtuuEDIfz4vbvUpJMBCLDG3Ft6YtK0+DApVp0
5MPhtB1LhPZhEH3BZUwmGlgtjH7ZVTNgr25DrFElkBD9bmdxH6xSLCrGzs3zzuz+
0+a2UigS+rcLHGnQA/9B+8quor/0HUUv2D68AbX7M9j9CKwYGYhYDlmvEyGLZz37
eceoZOGY8Voq9a/8HrOHcmxndjRQzx2takCQiYCUKazoeoQcbaP8uLefnNlcbJp7
psu5hAM6+KZceZ8GXoON9uO0Cj3tQA==
—–END CERTIFICATE—–
subject=/OU=Domain Control Validated/CN=cc.sedoparking.com
issuer=/C=BE/O=GlobalSign nv-sa/CN=GlobalSign Domain Validation CA – SHA256 – G2
—
No client certificate CA names sent
—
SSL handshake has read 2716 bytes and written 641 bytes
—
New, TLSv1/SSLv3, Cipher is AES256-SHA
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1
Cipher : AES256-SHA
Session-ID: ACE8E9B4C38D3B63359EEB4016C2FA3424AEC582ABCE4E293C92E4E717CD7D26
Session-ID-ctx:
Master-Key: 3B26FC8251A071FEB876387781B1D49DAF22EB2612B2C61BCB6DCE346CDE59B71EF8D0DCF072BFAE4B1AD331CA579C9A
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket:
0000 – e0 16 d4 ce bb fb b5 cb-32 ef 2c b2 0d a0 a9 76 ……..2.,….v
0010 – 2b 59 82 09 1f 78 a3 67-ca 14 23 00 66 22 d6 8d +Y…x.g..#.f”..
0020 – 01 2d d7 eb 76 4b 99 47-ad 29 10 52 7f 2f a3 e1 .-..vK.G.).R./..
0030 – a3 46 80 a4 dc 2f df b7-c6 a0 07 43 53 7d 4e d7 .F…/…..CS}N.
0040 – 61 c1 a8 0a c5 f4 eb 6d-3c eb 8e 76 24 94 04 99 a……m<..v$…
0050 – e8 3d eb cb f1 ba b1 0f-ff 24 59 2f cf d5 f0 50 .=…….$Y/…P
0060 – 83 4d 28 54 b8 c5 38 b6-bc d6 f6 8f 9d 45 9c 59 .M(T..8……E.Y
0070 – 62 36 75 4c e4 a8 8b 30-79 1f 24 be 36 93 57 24 b6uL…0y.$.6.W$
0080 – 44 84 dc c0 04 3c b0 0d-9c 09 2b 61 14 c4 bf 06 D….<….+a….
0090 – 4d 60 79 90 11 49 cf 86-f0 bc 74 16 de f3 fe e3 M`y..I….t…..
Start Time: 1462909951
Timeout : 300 (sec)
Verify return code: 0 (ok)