- Generate Root Certificate key.
openssl genrsa –out RootCA.key 4096
- Generate Root certificate.
openssl req –new –x509 –days 1826 –key RootCA.key –out RootCA.crt

- Generate Intermediate CA certificate key
openssl genrsa –out IntermediateCA.key 4096
- Generate Intermediate CA CSR.
openssl req –new –key IntermediateCA.key –out IntermediateCA.csr
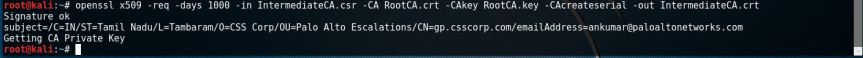
- Sign the Intermediate CA by the Root CA.
openssl x509 –req –days 1000 –in IntermediateCA.csr –CA RootCA.crt –CAkey
key – CAcreateserial –out IntermediateCA.crt
- Generate Server certificate key
openssl genrsa –out Server.key 2048

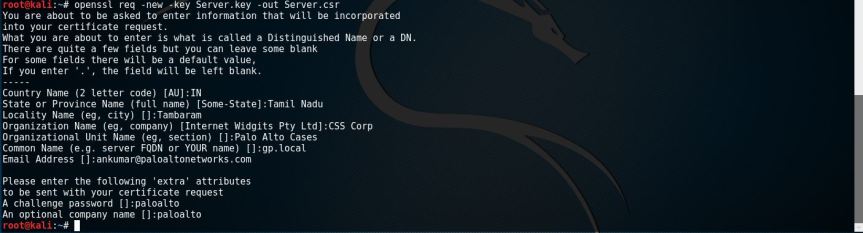
- Generate Server certificate CSR.
openssl req –new –key Server.key –out Server.csr
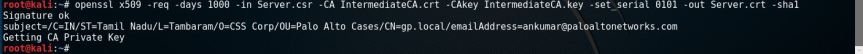
- Sign the Server Certificate CSR using the Intermediate CA.
openssl x509 –req –days 1000 –in Server.csr –CA IntermediateCA.crt –CAkey
key – set_serial 0101 –out Server.crt –sha1
NOTE:
A. This is an add-on for Linux system, especially in cases where you will have to import the certificates in the cert store of Linux systems.
Copy the certificate in the trusted store in Linux:
Root# cp *.crt /usr/local/share/ca-certificates/
Root# update-ca-certificates

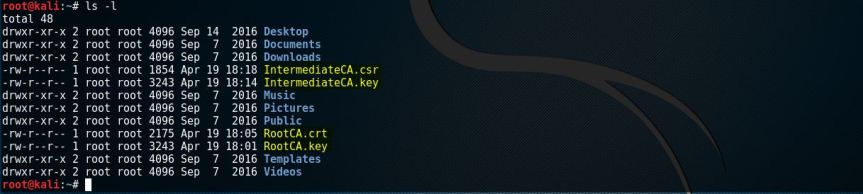
B. To view the key or the certs or the csr generated as per the steps mentioned above use the command “ls”.
Root# ls -l
C. Verify the certificate.
openssl x509 –in Server.crt –noout –text | grep ‘host.local’